
You may have noticed tiny transactions in your wallet, like 0.00000001 BTC or 0.0001 USDT. These small amounts might seem insignificant, but they serve various purposes—benign and risky. Let’s explore what these transactions mean for your business.
Privacy Analysis and Address Tracking
Purpose: Track fund flows and compromise user privacy
Method:
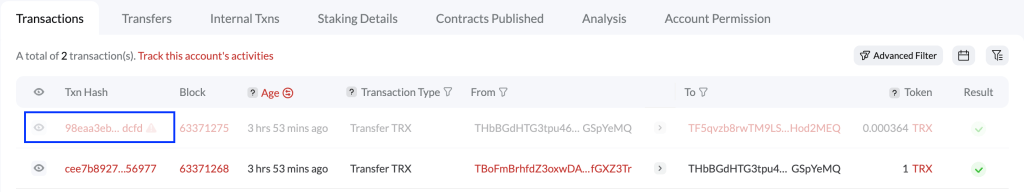
On UTXO-based blockchains like BTC and BCH, attackers send small transactions, such as 547 or 888 satoshis, to target addresses. When users mix these small amounts with identified UTXOs, attackers trace the connection between anonymous addresses and real identities, revealing the owner.
Contact Cactus Custody to freeze dust transactions and prevent tracking if you detect them.
(Example: A transaction sends 888 satoshis of dust to thousands of addresses.)

Phishing and Scamming
Purpose: Attract users to malicious websites or engage them with attackers
Method:
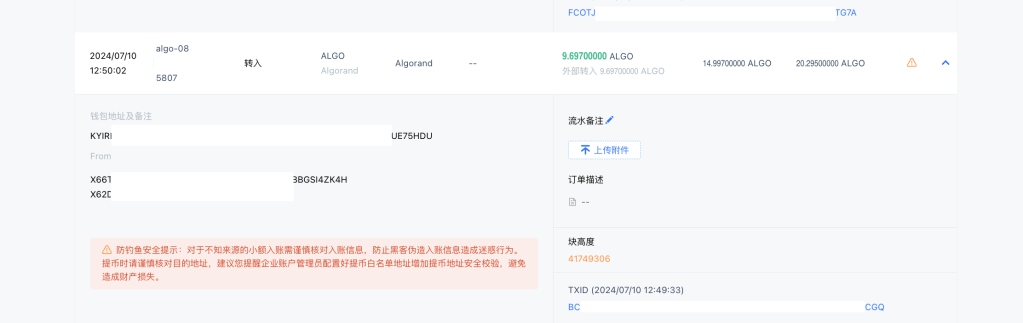
Attackers send small amounts to grab the victims’ attention, prompting interaction with the attackers’ addresses. Tactics include address spoofing and fake airdrops.
To safeguard against these threats, avoid interacting with suspicious transactions. Cactus Custody provides alerts for small incoming transactions, and many blockchain explorers offer similar warnings. Stay vigilant to protect your assets.

For insights on fake airdrops and phishing transfers, review these articles:
What Are Airdrop Scams and How to Avoid Them
What Is a Transfer Phishing Attack
Advertising and Marketing
Purpose: Capture user attention and promote new projects or services
Method:
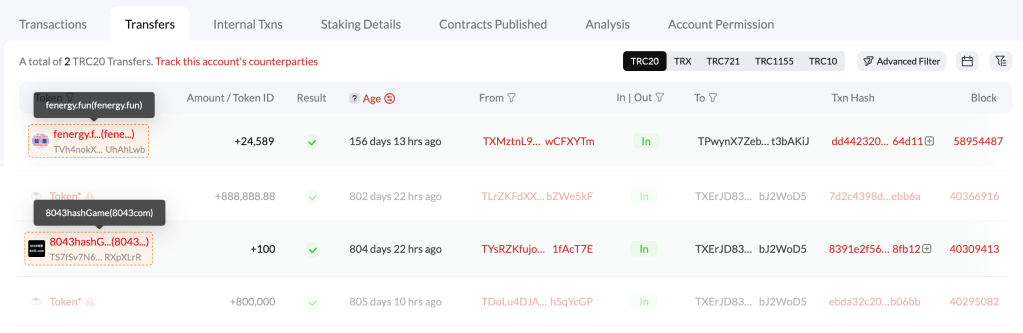
Project teams send small transactions with specific information to active blockchain addresses, directing users to their project websites or sparking curiosity.
While these deposits aren’t malicious, they resemble phishing airdrops, making them hard to identify and risky. Cactus Custody advises ignoring these promotional messages or approaching them with caution.
We discovered some promotional transactions randomly (Cactus Custody remains neutral and does not endorse or criticize these projects).
DDOS Attacks
Purpose: Overwhelm a network or system
Method:
Attackers flood the network with numerous transactions to consume resources, temporarily rendering the blockchain or system unavailable. For example, in August 2018, hackers used a DDOS attack on the popular Ethereum game Fomo3D, forcing it to end and claiming all prizes. Similarly, the Solana chain has experienced DDOS attacks, causing several hours of outages.
Cactus Custody offers robust protection against DDOS attacks. Given the high cost and difficulty of launching on-chain DDOS attacks, such incidents are rare and should not be a significant concern.
Contact Cactus Custody to ensure your business remains secure from these threats.